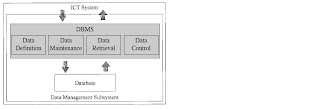
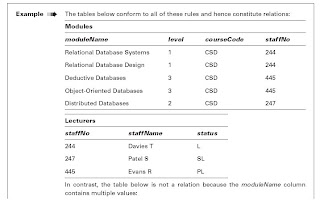
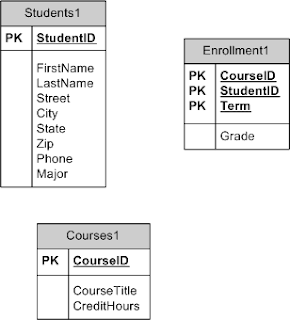
The Importance of System Development
System development can mean to compile a new system to replace a whole old ones system or to improve or to repair the system. Mentioned matter can be caused of several things:
1. Existence of problems.
Problems can be arising from:
a. Unfinished problem.
That is:
- intended deceivingly which can cause of danger to the properties and the truth of company data become less guaranteed.
- mistake which do not be intended which also can cause the truth of data become less guaranteed.
- inefficient of operation
- do not adhere of policy of management which has been specified
b. Growth of Organization. Growths of organization can cause of compile new system. The example is requirement of information which become progressively wide, data-processing volume become progressively mount, and change of new accountancy principle.
2. To reach for opportunity
Organizational start to feel that this information technology require to be ready to used to increase information so that can support in course of decision making to conducted by upstairs management.
3. Existence of Instruction
Compilation of new system earn also happened caused of instruction upstairs management level or from outside organization.
Besides things above there are also other indicator which cause system old ones have to change, among others:
- Sigh of customer/ client.
- Delivery of goods which often delay
- Payment of salary which often lose time
- Inopportune report
- Report content which is wrong often
- Indistinctness responsibility
- Abundant in working
- Low labor productivity
- Lose time market interest
- High operating expenses
- Inefficient investment
The Purpose of Developing an Information SystemAfter developing new system, expected improvement in new system. This improvement relate to PIECES, that is:
- Performance, improvement of new system performance so that more efficient. Performance can be measured from throughput and response time. Throughput is the amount of work which can be done certain in a moment. Response Time is average time which delays among two work added with response time to answer the work.
- Information, improvement of quality of presented information.
- Economic, improvement of advantage or benefit.
- Control, improvement of controlling for detecting and repairing some mistake and also insincerity.
- Efficiency, improvement of operating efficiency.
- Service, improvement of service given by system.
Principle of System Development.1. The system is developed for management.After the systems have been developed, furthermore which must be done to use this information system for management.
2. The system is developed for big capital investment.The developed system represent big capital investment, hence which have to consider two matters on the following:
- All existing alternative have to be investigated. All ekonom mention it with opportunity cost term. If there are some chosen investment that can be inculcated, hence the choice must be at highest investment of its advantage storey.
- Good investment has to be valuable. The best chosen investment of course not represent most beneficial. Investment told to profit if its benefit or result of returning is bigger than expense to obtaining it.
3. Developed system needs one who is educated.Educated of its intention non meaning graduated to college. But its intention earn has be done on the job training. Besides a system analyst have to education to problem of which is faced it.
4. Step work and duty must be done in course of system development.Its intention is before system development process is done, hence have to be made beforehand job schedule that showing step work and duty to be done, so system development process can be done and finish successfully as according to planned budget and time.
5. Process system development doesn’t have to sequence.The example, at the time of conducted hardware levying, meaningless the other process system development is discontinued just for waiting the hardware which it’s required, but can be done by other scheme which is not irrespective hardware existence.
6. Don't be afraid to cancel the projectAt certain moments, where a project have to be discontinued or canceled because have improper again, hence must be done emphatically. Doubtfulness in running the project which have improper can cause permeating its of useless fund.
7. Documentation must be for guidance in system development.Documentation is very important matter in development system. Often happened to some analyst system, documentation processing at the end of system development process, even worse they do not have documentation. Documentation which is made and collected during development system process can be used for communications between analyst system within user and can be used to push involvement of user.
System Development Life Cycle1. WaterfallModel RequirementAt this phase happened is gathering the requirement of system base. The examples are software, human being, and database. This phase also include, gathering of requirement at strategic business storey level and business area storey level.
DesignThis Phase is process which focusing at four attributes: data structure, system architecture, interface representation, and algorithm. This phase is translate requirement process into software representation.
ImplementationDesign have to be translated into machine language form. The making of code step reside in this phase. If the design completely done, making the code can be finished mechanically.
VerificationAfter made the program code, program examination is started. Examination process focus at internal logic software, examination to find mistake and ascertain input is limited that will give result of appropriate actual.
MaintenanceThis Phase is system maintenance process. System possibly will experience of change after submitted to customer.
 2. Iterative Model
2. Iterative ModelIt does not far different from waterfall model. Model iterative even also have phase at the time of planning, and analysis of design, implementation, and launching. But this model form is a cycle. There are conducive evaluation phase of system which make improve or repair, if still there are some mistakes, then return to planning phase to yield better system.
 3. Spiral Model
3. Spiral ModelModel Spiral initially proposed by Boehm [ BOEHM88]. Model spiral is software process model which is evolutional which stringing up the nature of iterative model and the systematic nature from the waterfall model. This model contain six duty region **:
Customer Communications: duty which is required to develop effective communications among customer and developer.
Planning: duty which is required to define resource, accuracy of time, and other related information.
Risk analysis: duty which is required to appraise good risk of management and also its technical.
Engineering: duty which is required to develop one or more representation the application.
Construction and launching: duty which is required for construction, testing, installing, and giving service to user.
Customer evaluate: duty which is required to obtain feed back from customer.
**Source: Pressman, Roger S., Ph. D., Software Engineering: A Practitioner’s Approach, Mcgraw-Hill, 1997, page. 47. 4. RAD (Rapid Application Development) Model
4. RAD (Rapid Application Development) ModelRAD is a growth process model of software which emphasizing very short growth cycle. Phase process RAD shall be as follows:
Business ModelingWhat’s information controlling business process? Who’s peep out? Who’s processed? These questions is what kind of information which related to business.
Data ModelingInformation which have been modeled to be defined into data form. The data will be processed at next phase.
Process ModelingData which have been collected mentioned is hereinafter processed. This process include: adding, lessening, modifying.
Application GenerationData which have been processed to be required at the time of making application. Application made with high level programming language so that yielded application can be used better.
Testing and Turnover RAD process emphasize at usage return, therefore many examinee program component. Besides at this phase, the customer / client have to be trained by the way of using it.
 Approach of System Development
Approach of System DevelopmentThere are some approach for the system development:
1. Classical approach against structured approach ( looked into used methodologies). Classical approach methodologies is developing system by following steps in system life cycle. This approach emphasize that system development will succeed if or when following step in system life cycle.
1.1 Classical approach
Classical approach also referred as traditional approach or conventional approach. This approach follows steps in system life cycle without supplied with adequate techniques and appliances. Problems can arise in classical approach are:
- Software development become too difficult.
- System maintenance cost become costly.
- Possibility of happened mistake very big.
- Efficacy of system less guaranteed.
- Problem at applying the system.
1.2 Structured Approach
This approach must be the same with classical approach. The difference is the structure follows steps in system life cycle supplied with techniques and appliances which have is adequate.
2. Piecemeal approach against system approach (looked into the target to reach).
Piecemeal approach represent approach of system development emphasizing at just certain application or activity. This approach only paying attention target to application or activity.
System approach pay attention in information system as one unity to the each activity or its application. This approach also emphasize at overall goal achievement from organization.
3. Bottom-up approach against Top-down approach (looked into the way of determining requirement of system).
Bottom-up approach started from formulation of requirements to handle transactions and climb level by formulating requirement of information pursuant the transaction.
Top-down approach is distinct from under-up approach. This approach is started from defining target and policy of organization, analyze requirement of information, until transaction process.
4. Total-system approach against modular approach (looked into the way of developing it).
Total-system approach represent approach totally developing system at a time. Modular approach, approach by breaking complicated system become some simple part, so that system will be more easy to comprehended and developed.
5. Great loop approach against evolutionary approach (looked into technology to be used).
Great loop approach apply totally change at a time use sophisticated technology. This change contain risk, because technology untimely expand. This approach also too costly because needs very big investment at the time levying the technology. Evolutionary approach apply sophisticated technology just for applications which need at that moment. The advantage is investment do not too costly but still can keep abreast of technology.
Methodologies System Development
Methodologies is unity of methods, procedures, work concepts, used postulates and rules of science, artistic or the other discipline.
Method is a way of systematic technique to do something. Methodologies system development mean is methods, procedures, work concepts, postulates and orders to be used to develop an information system. By following method or procedures given by an methodologies, hence system development expected will be able to be finished successfully. Procedure steps for this trouble-shooting is recognized with
algorithm term.
Three classifications of development methodology:
1. Functional Decomposition methodologies. This methodologies emphasize at resolving of system into smaller subsystems, so that will be more easy to be comprehended, to be designed and applied. Which included in this methodologies is:
- HIPO (Hierarchy plus Input-Process-Output).
- Stepwise refinement or Iterative stepwise refinement.
- Information-Hiding
2. Data-oriented methodologiesThis methodologies emphasize at characteristic of data to be processed. This methodologies is grouped into 2 class:
a. Data-flow oriented methodologies
This methodologies is in general relied on resolving of system into modules to from data element type and behavior of the module logic in system. Which included in this methodologies is:
- SADT (Structured Analysis an Design Techniques)
- Composite Design
- Structured systems and analysis and Design (SSAD)
b. Data structure oriented methodologies
This methodologies emphasize structure of input and output in system. Which included in this methodologies is:
- JSD (Jakson’s systems development)
- W / O (Warnier / Orr)
3. Prescriptive Methodologies.Which included in this methodologies is:
- ISDOS (Information System Design and Optimization System). Usefulness of ISDOS is automatization process system development of information. ISDOS have two component, these are PSL and PSA. PSL represent especial component of ISDOS, that is a language to note requirement of user to machine-readable form. PSA represent software package which look like with data dictionary and used to check entered data, which is kept, analyzed and yielded as report output.
- PLEXSYS. Its usefulness is to conduct a high level computer Ianguage transformation to an executable code to hardware configuration which wanted.
- PRIDE, representing a software which good to analysis / designed by structure system, data management, project management and documentation.
- SDM / 70, representing a software contain with method corps, estimation, documentation and guide of administration utilize to help user to develop and take care of effective system.
- SPECTRUM, representing methodologies of system development and have some version. SPECTRUM-1 (for conventional life cycle), SPECTRUM-2 (for structured project management system) and SPECTRUM-3 (for on-line interactive estimator).
Technique in System Development1. Project management technique is CPM ( Critical Path Method) and PERT (Program Evaluation and Review Technique).
This Technique is used for project scheduling.
2. Finding fact technique, that is technique able to be used to collect and find facts in study activity existing system. This techniques among others:
1. Interview
Advantages
a. Interview give opportunity to interviewer to motivate customer to answer freely.
b. Enabling interviewer to develop questions according to the situation that happened.
c. Interviewer can assess the truth of behavior of given answer.
Disadvantages
a. Interview process require so many time.
b. Tend to disturb the one who is held an interview.
2. Observation
Advantages
a. Collected data very accurate.
b. System analyst easier to process collected data.
c. Work storey level can be measured.
Disadvantages
a. Can bother observation object
b. Observation can bother work which is doing.
3. Questionnaire
Advantages
a. Questionnaire good to resource which is many and spread over.
b. Responder do not feel annoyed.
c. Relative more efficient.
d. its result more objective.
Disadvantages
a. Questionnaire do not guarantee responder to answer the question better.
b. Tend to inflexibility.
c. Complete questionnaire difficult to be made.
4. Gathering sample
3. Cost-effectiveness analysis techniqueThis technique emphasize that advantage of information system development not all can be measured directly with money value, like for example advantage of better service to the customer. But, if we like to determined with money value, hence can appraise its effectiveness.
4. Meeting techniqueDuring conducted system development process, oftentimes meeting performed either by developer team with user and manager. Intention of meeting is to:
- Defining problem
- Collecting ideas
- Solving problems
- Finishing conflict that happened
- Analyzing progress of project
- Collecting fact or data
5. Inspection techniqueProcess from analysis and designed system have to observe. Observation of management represent matter which is very needed. Intention of inspection is to assure that documentation which have been made by developer team is competent and correct technique.
System analyst and programmer Following is difference between system analyst and programmer:
Programmer - Responsibility only limited to making of computer program.
- Programmer knowledge limited enough to computer technology, computer system, utilities, and programming Ianguage.
- Its work have technical and have to precisely in making instructions program.
- Its work do not concerning relation with many people, limited to each programmer and system analyst.
Analyst System - System analyst responsibility do not only at making computer program, but at a whole system.
- Its knowledge have to wide, not only at computer technology, but also at the other application area.
- Its work in making of program limited to trouble-shooting marginally.
- Its work entangle many people relation, does not limited to each system analyst, programmer, but also with user and manager.
Knowledge and needed by system analyst - Knowledge and membership about data-processing technique, computer technology and computer programming.
- Knowledge about business in general. This knowledge is required so that system analyst can communicate with user. This knowledge cover financial accounting, cost accounting, accounting management, management operation system, marketing, and other business aspects.
- Knowledge about quantitative method. In developing application models, system analyst using many quantitative methods, like for example linear programming, dynamic programming, and others.
- Expert of trouble-shooting. System analyst must have ability to put down complex problems into parts of small and then solving it.
- Expert of communications between personnel. System analyst must have ability of communications, either through oral and also article.
- Capable to construct relation between personnel. Constructing good relation between personnel can improve team performance. That thing represent responsibility from a system analyst.